NetShop ISP Announces Beta Launch of Recipes: Empowering Customers with Server Automation Tools
NetShop ISP, a leading provider of cutting-edge hosting and data center solutions, is excited to announce the beta release of Recipes, a powerful automation tool integrated into the myNetShop portal. Recipes empower customers to automate server tasks effortlessly using a range of pre-programmed actions, improving efficiency, user experience and simplifying server management.
NetShop ISP, a leading provider of cutting-edge hosting and data center solutions, is excited to announce the beta release of Recipes, a powerful automation tool integrated into the myNetShop portal. Recipes empower customers to automate VPS and Dedicated server tasks effortlessly using a range of pre-programmed actions, improving efficiency, user experience and simplifying server management.
Recipes: A Breakthrough in Server Automation
Recipes is a feature-rich offering within the myNetShop portal that simplifies server management by allowing users to automate various tasks using pre-programmed actions. This innovative tool is designed to meet the diverse needs of our customers, from tech-savvy IT professionals to business owners, without much server management experience, looking for user-friendly automation options.
Key features and benefits of Recipes include:
- Seamless Automation: With Recipes, customers can automate a wide range of server tasks with just a few clicks, reducing the risk of human errors and streamlining operations.
- Pre-Programmed Actions: Choose from a library of pre-configured automation actions, making it easy to set up, customize, and deploy automated processes tailored to your specific needs.
- Time and Cost Savings: Automation leads to increased efficiency and reduces the time and resources required to manage servers, ultimately saving customers both time and money.
- Reliability and Consistency: Automation eliminates variability in task execution, ensuring that server tasks are carried out consistently and reliably.
- User-Friendly Interface: The myNetShop portal’s intuitive interface simplifies the automation process, enabling users to create and manage Recipes without the need for advanced technical, server administration skills.
NetShop ISP’s CEO, Stefano Sordini, stated, “The beta launch of Recipes reflects our commitment to delivering innovative hosting solutions that empower our customers to succeed in a dynamic digital landscape. Automation is no longer a luxury but a necessity, and Recipes is our answer to the growing demand for reliable and user-friendly server automation tools.“
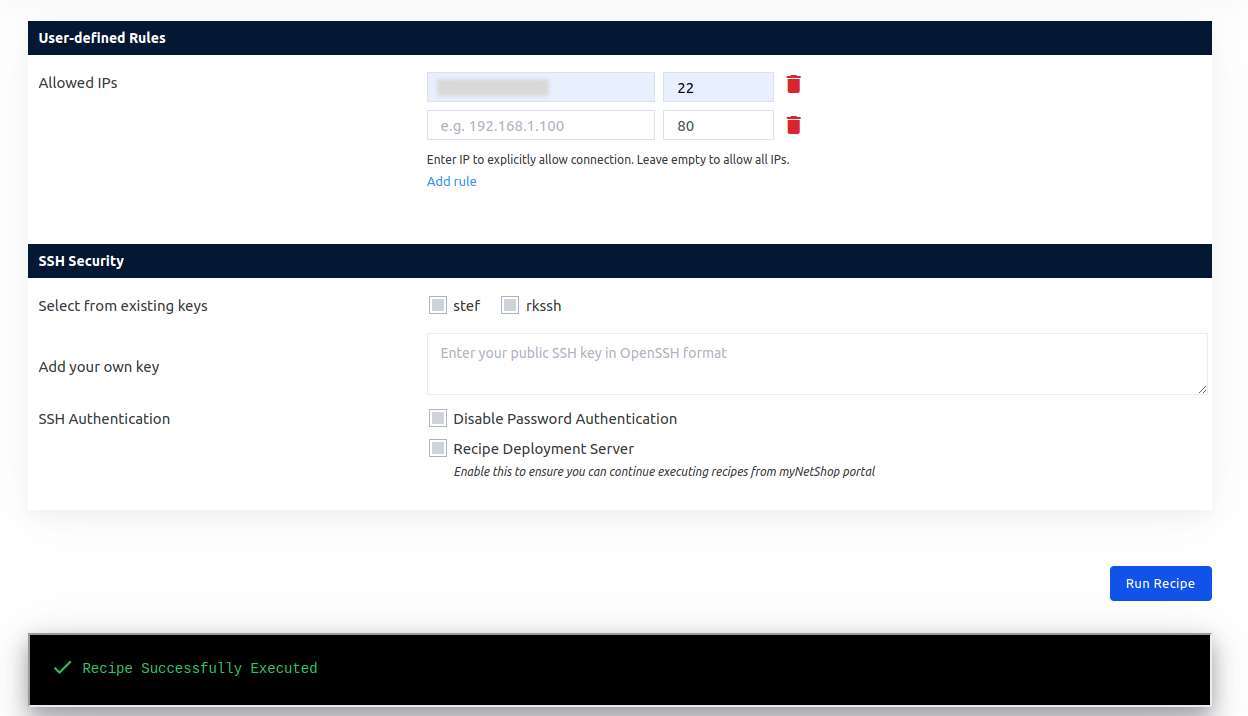
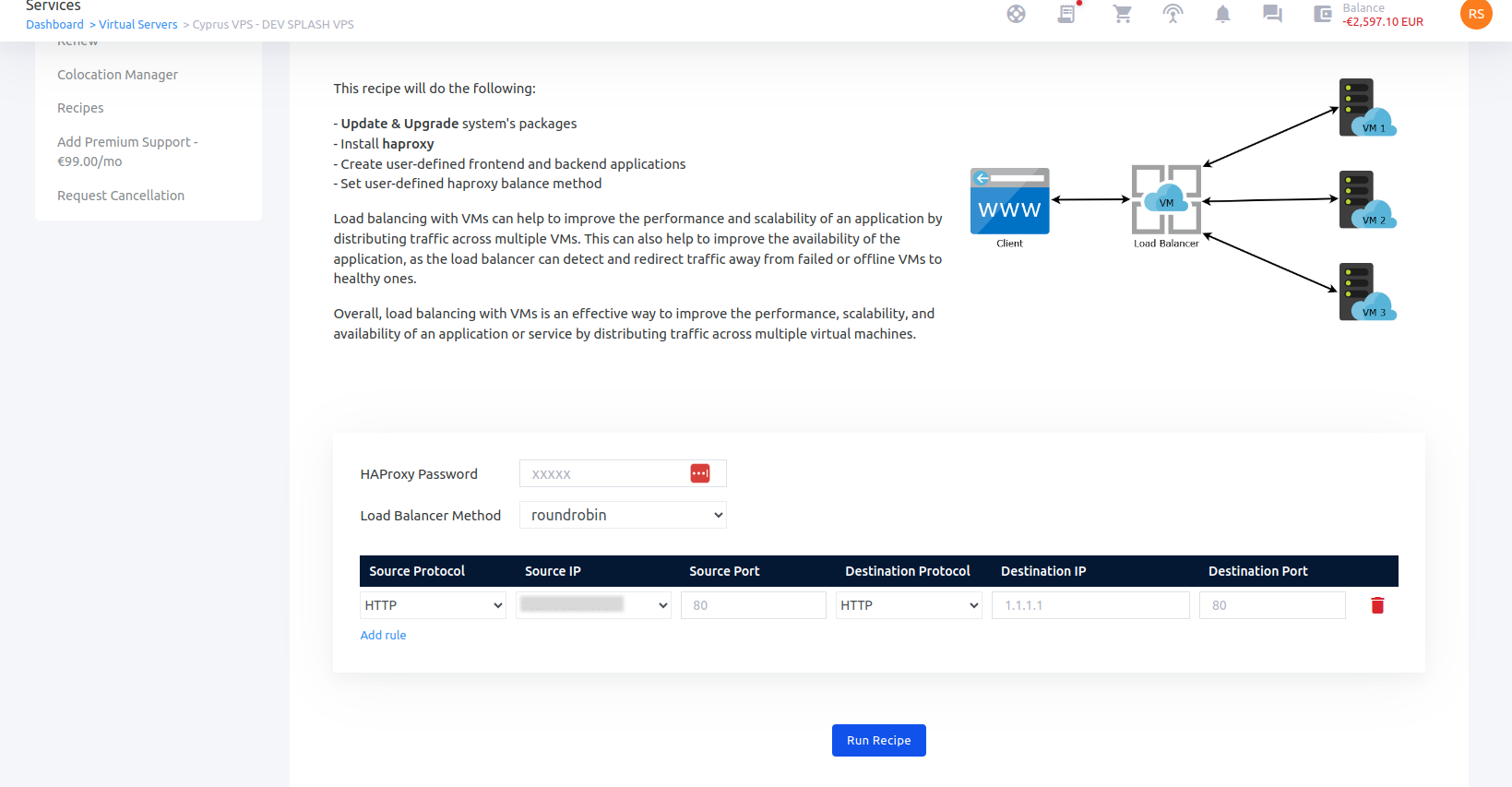
How to Access Recipes
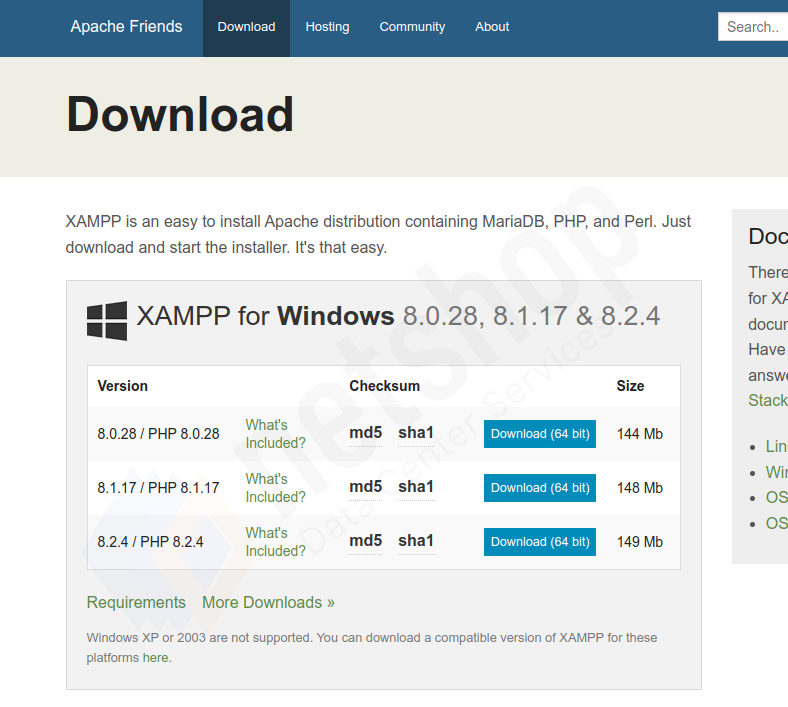
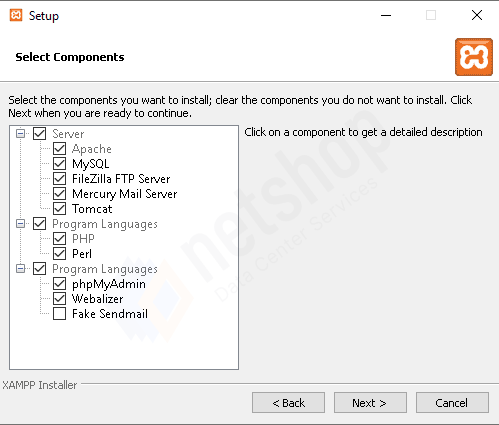
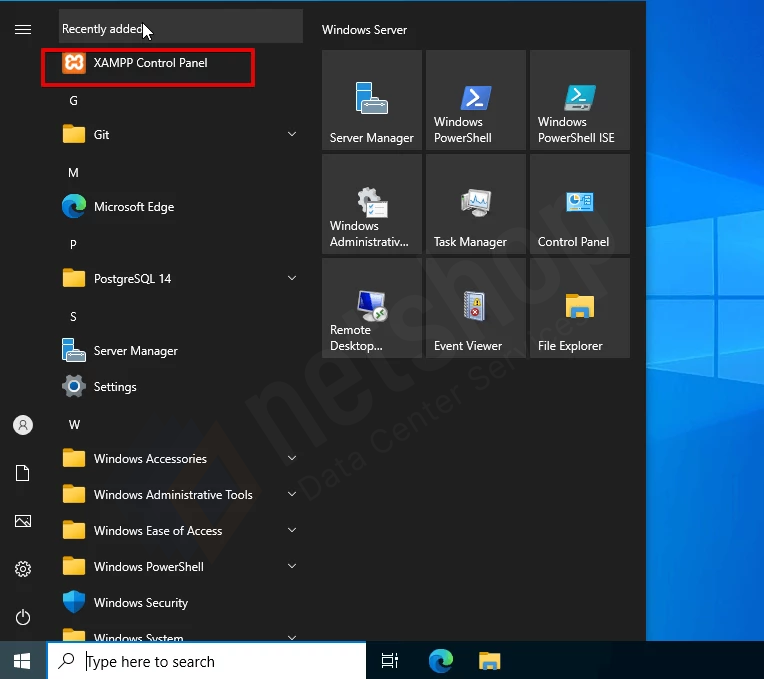
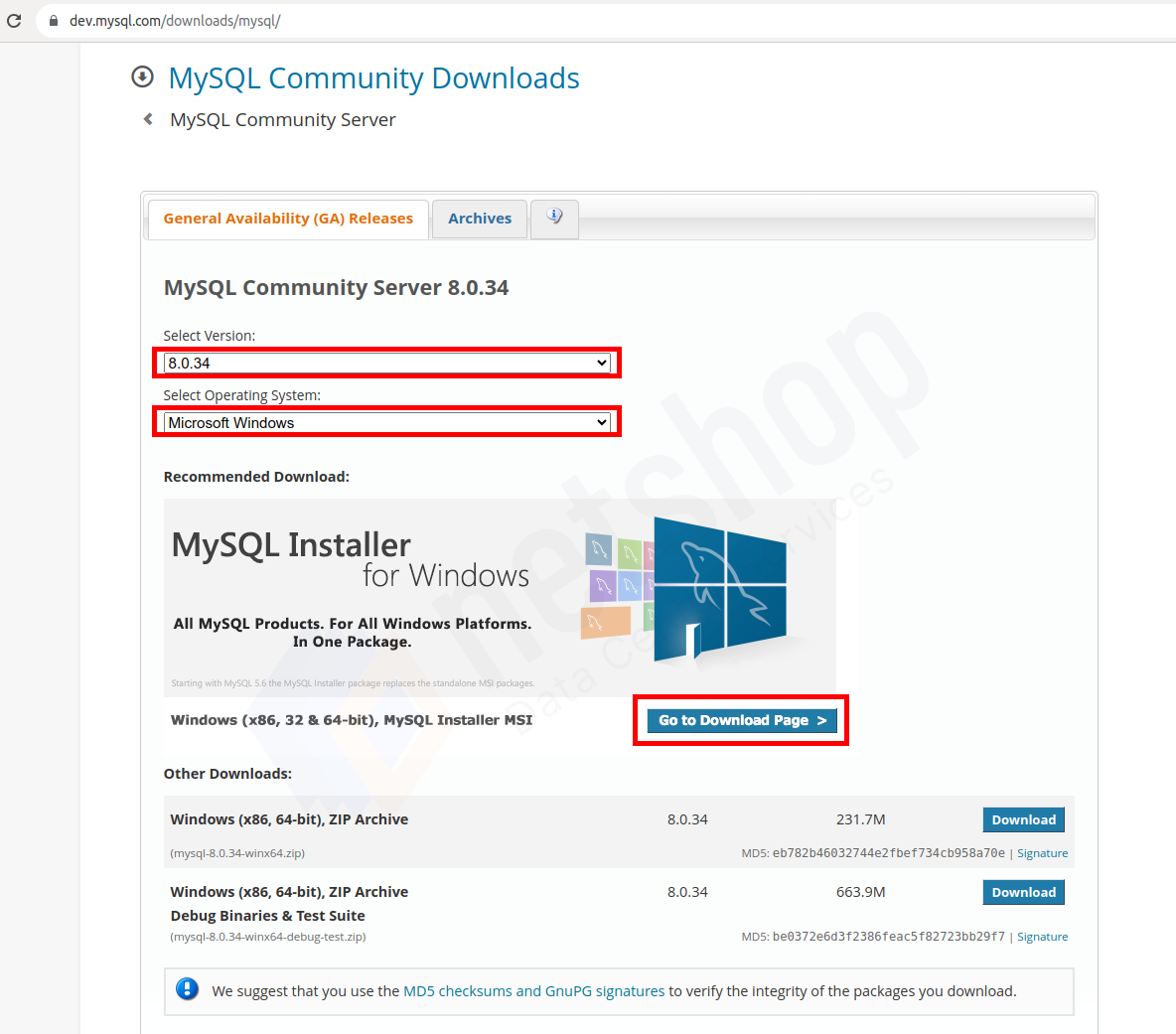
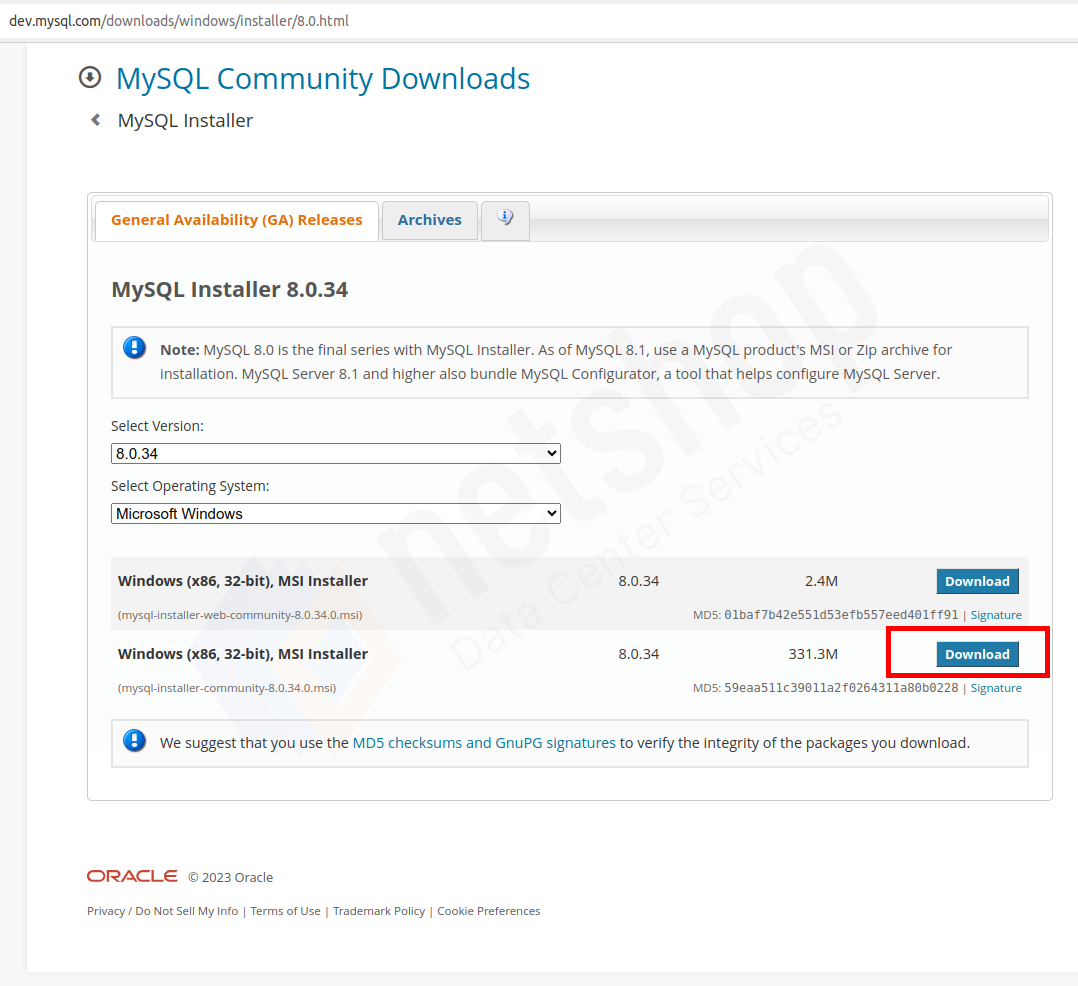
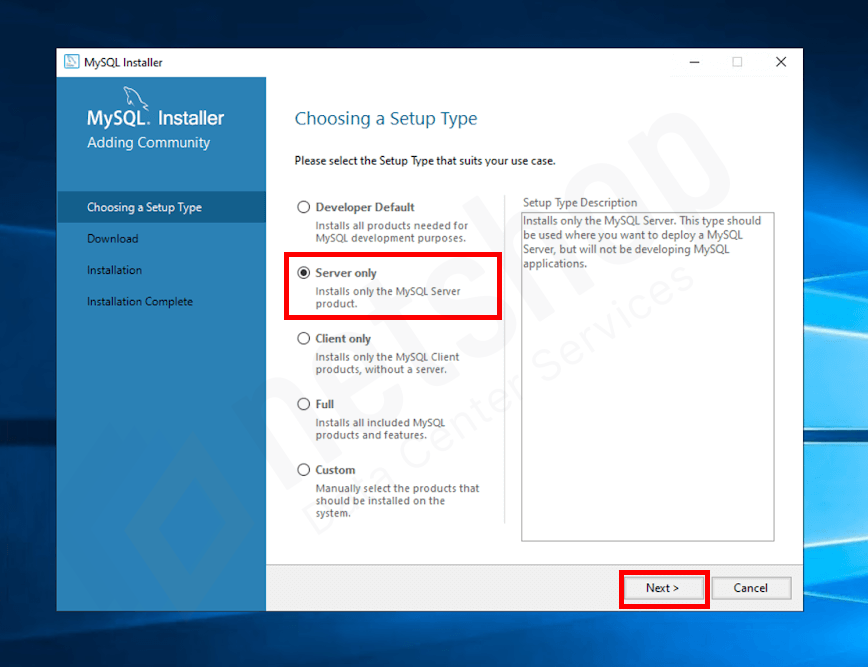
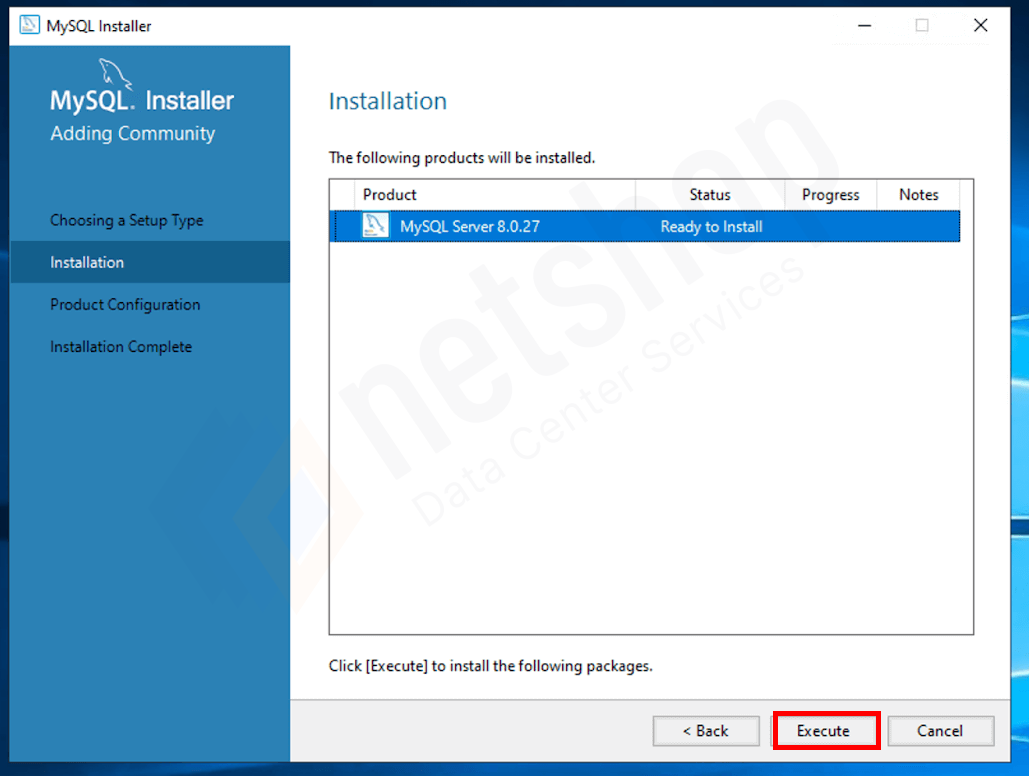
To access Recipes, NetShop ISP customers can simply log in to the myNetShop portal and navigate to the Server (Dedicated or Virtual) management page. Recipes can be found on the left-hand side Services menu. From there, they can explore the library of pre-programmed actions and execute Recipes tailored to their specific server management needs.
Beta Testing Phase: Your Feedback Matters
During the beta testing phase, NetShop ISP welcomes user feedback to further refine and enhance the Recipes feature. Customers are encouraged to provide insights, report any issues, and suggest improvements to help shape the final version of Recipes.